
Windows
Active Directory Lab
Windows Server 2022

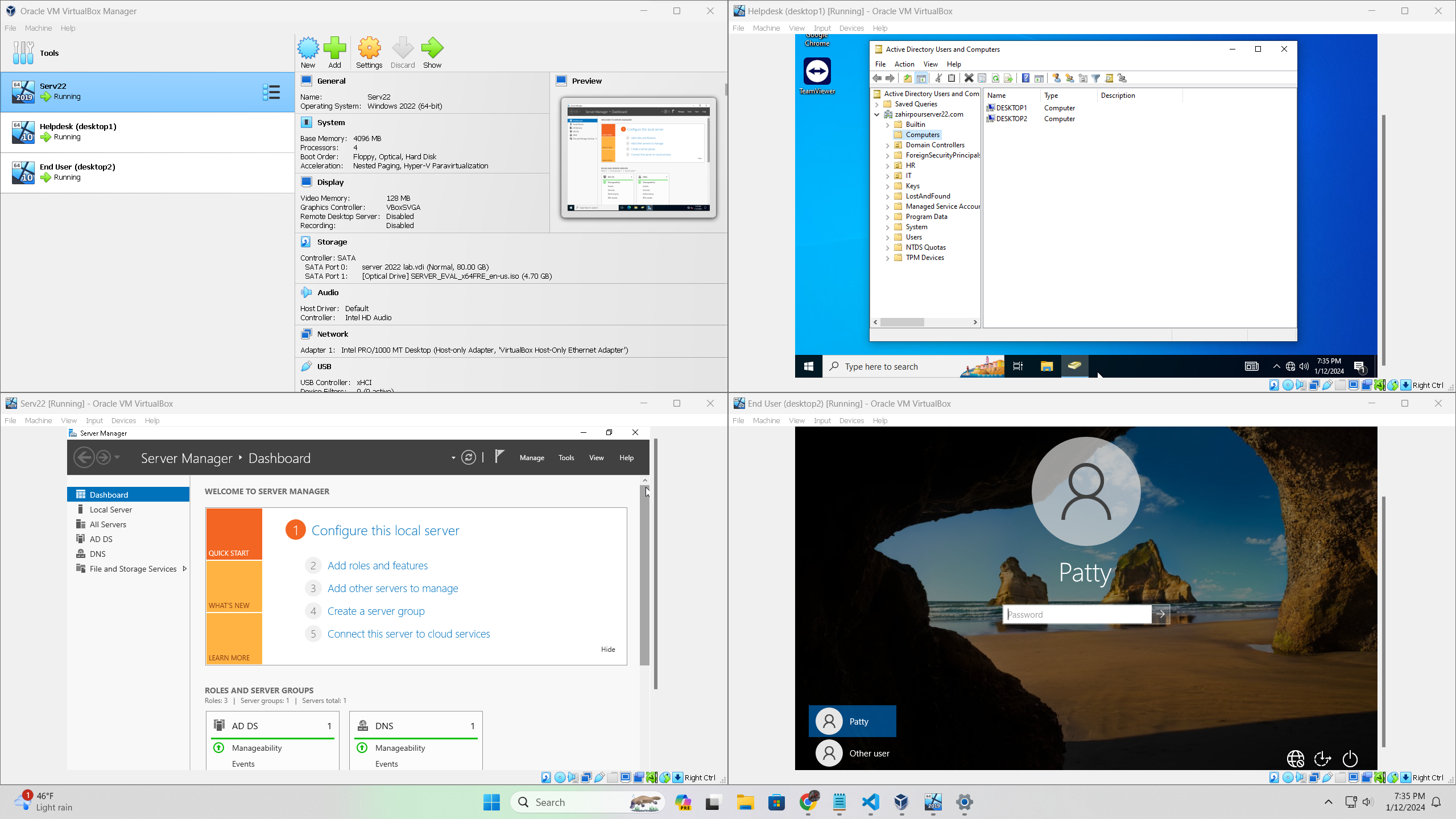
For my first project, I undertook a comprehensive exploration of Active Directory with the aim of enhancing my readiness for future professional roles. I set up three virtual machines with specific roles: one as a server, another for a helpdesk account, and the third for a user account. These machines were integrated under a common domain, allowing for the introduction of troubleshooting scenarios for the user account. Subsequent resolution exercises were performed using the helpdesk account. For a step by step guide on how to recreate the Active Directory lab environment check out my Github!
- Downloaded VirtualBox and the free Windows Server 2022 evaluation (valid for 180 days).
- Installed the server within a virtual machine with precise resource allocations (4GB RAM, 4 cores, 50GB storage).
- Configured the server with the user-friendly name "serv22" and secured it with the password "Password123!".
- Installed Active Directory Domain Services using "roles and features."
- Established a new forest, setting the Directory Services Restore Mode password to "Password123!".
- Enabled the recycling bin feature in the "Active Directory Administrative Center."
- Created a new domain account named "helpdesk" by copying the administrator account.
- Created a brand new domain account named "Patty" to be the end user we are supporting.
- Utilized the command "net user "user name" /domain" to verify account status, password expiration, and group memberships.
- Downloaded and installed Windows 10 Pro on two new virtual machines.
- Configured the VM's network setting to a host-only adapter.
- Completed the installation of the Windows 10 Pro accounts on two VM's with the username "user" and password "Password123!".
- Enabled the Administrator account, logged into it, deleted the "user" accounts, and installed "RSAT Tools" and "TeamViewer" on the helpdesk computer.
- Changed the computer names to "desktop1" and "desktop2" and join the domain (after changing the network settings in the following step).
- Adjusted the server's IP address from DHCP to static (10.1.10.2) with specified network parameters.
- Utilized Group Policy Manager to implement domain policies, such as password lockout and maximum password age.
- Modified the two new computer's network settings to static with the ip address's (10.1.10.3) & (10.1.10.4)
- Conducted network troubleshooting, ensuring proper communication between "serv22", "desktop1", and "desktop2" by adjusting network settings.
- Executed deliberate failed login attempts on "desktop2," entering the wrong password 10 times to trigger an account lockout.
- Utilized the "helpdesk" account to unlock "Patty's" account.
- Disabled and subsequently enabled "Patty's" account.
- Reset "Patty's" password, adhering to the current password policies.
- Implemented account manipulations:
- Expired "Patty's" account by setting the expiration date to the previous year.
- Effectively un-expired "Patty's" account.
- Conducted computer management actions:
- Deleted "desktop2" from the "Computers" Organizational Unit inside "Active Directory Users and Computers".
- Enabled "desktop2" from within the "Computers" Organizational Unit.
- Deleted the "desktop2" from the domain, logged into "desktop2" as the local administrator account, and left the domain.
- Successfully rejoined "desktop2" to the domain.
This ongoing project has not only deepened my understanding of Active Directory but also my proficiency in virtualization, network configuration, and systematic troubleshooting. As I continue working on this project, I plan to expand its scope and gradually incorporate additional elements. I will keep this post updated with the latest developments in this ongoing project.
 Active Directory Domain Services
Active Directory Domain Services